What is a Cryptographic Algorithm?
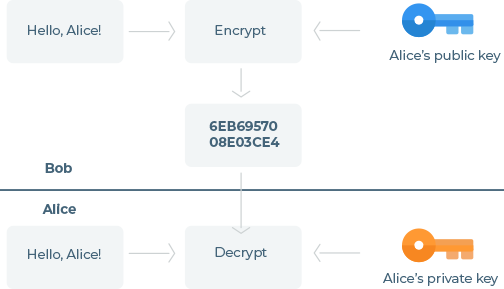
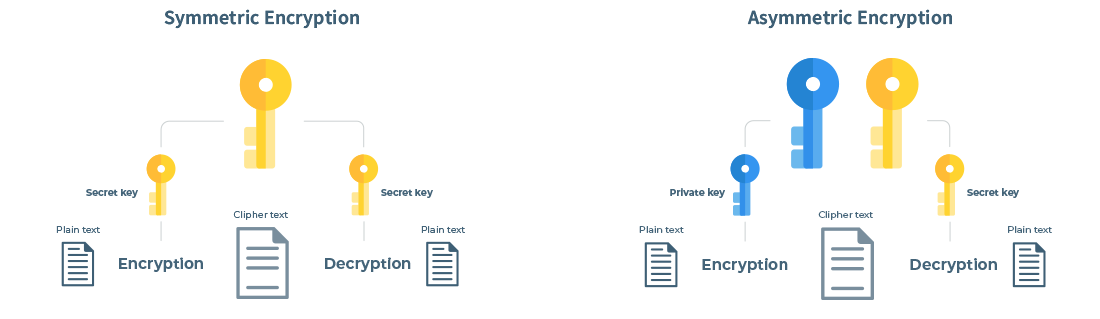
Cryptographic algorithms are what brings the crypto into cryptocurrency. Those algorithms are used when encrypting and decrypting your private address to a public address. An important aspect of those algorithms is its non-reversibility. Having your private address as input by applying the cryptographic algorithm you can easily get your public address as output, but doing the calculation in the reverse order, having the public address and applying the algorithm to get to the private address is an impossible task that will take many years to compute. Cryptographic algorithms are also what controls the difficulty of the blockchain by making it harder or easier to reach a consensus on the network. Cryptographic algorithms are made up of one, two or more hashing functions. Let’s now look at what a hashing function is.
How to sign into a Cryptocurrency Exchange?
In the simplest terms, an algorithm is a set of rules or steps to be followed when approaching a problem-solving task. It is important to clear out from the beginning, there are two types of algorithms – both simply referred to as algorithms where the confusion comes from – cryptographic algorithms and consensus algorithms. Both types serve a crucial function in the blockchain, but both are two very different things.
What are Consensus Algorithms?
Consensus algorithms are in the core of cryptocurrencies and allow the network to remain decentralized but at the same time continue to be fair. There are several consensus algorithms out there, all serving different purposes and most importantly having different criteria by which they decide how to reach a consensus. The two most common and widely used ones in crypto are proof of work (the algorithm used in bitcoin network where it all started) which reaches an agreement based on who has done the most “work” – meaning solved a mathematical problem the quickest; and proof of stake which reaches an agreement based on who has the most in stake in the blockchain. By now, you might be asking yourself, but why do we need algorithms at all. The two following paragraphs will answer that question.